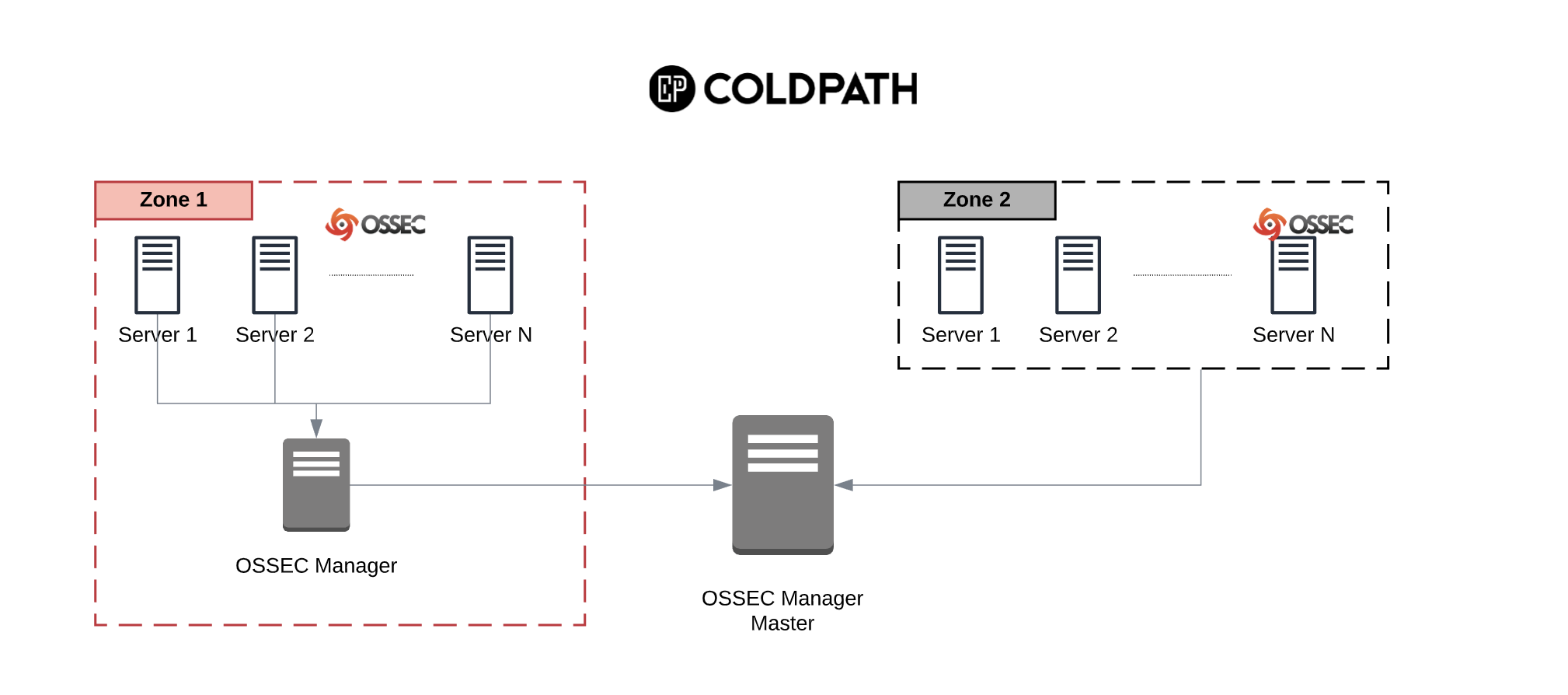
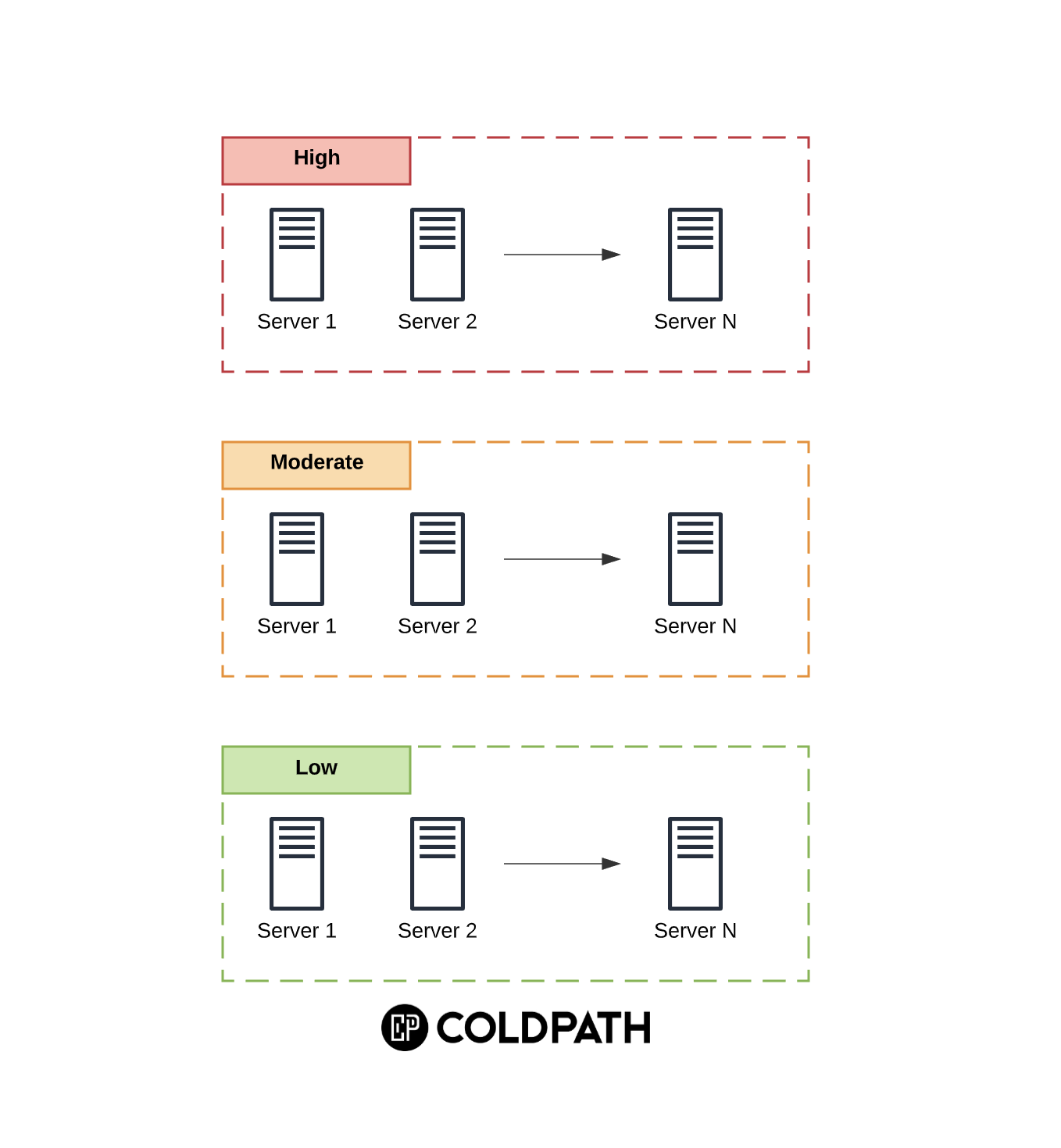
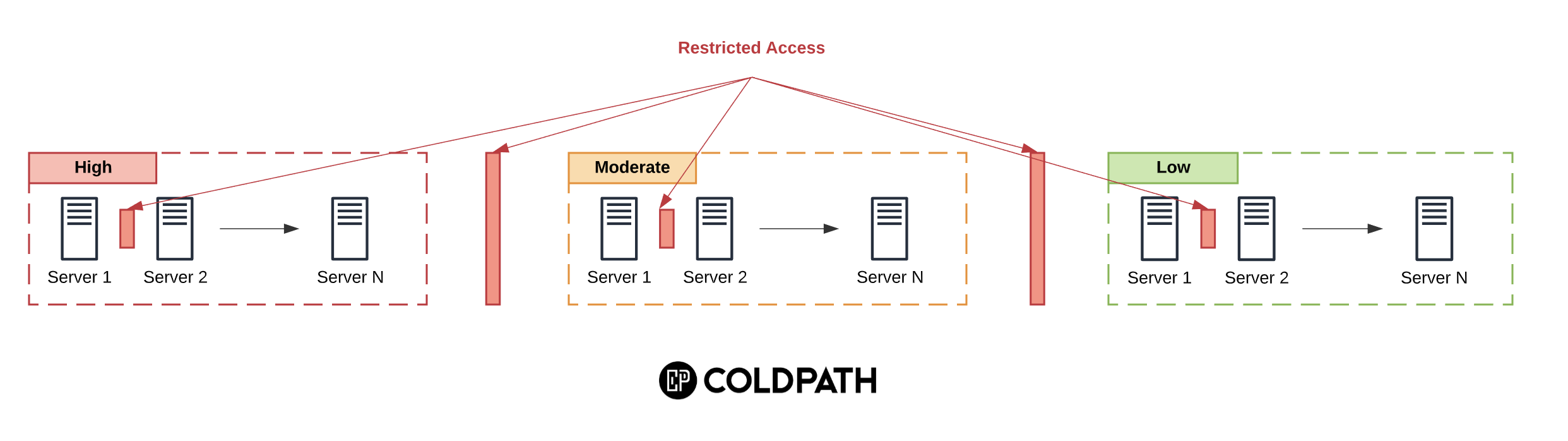
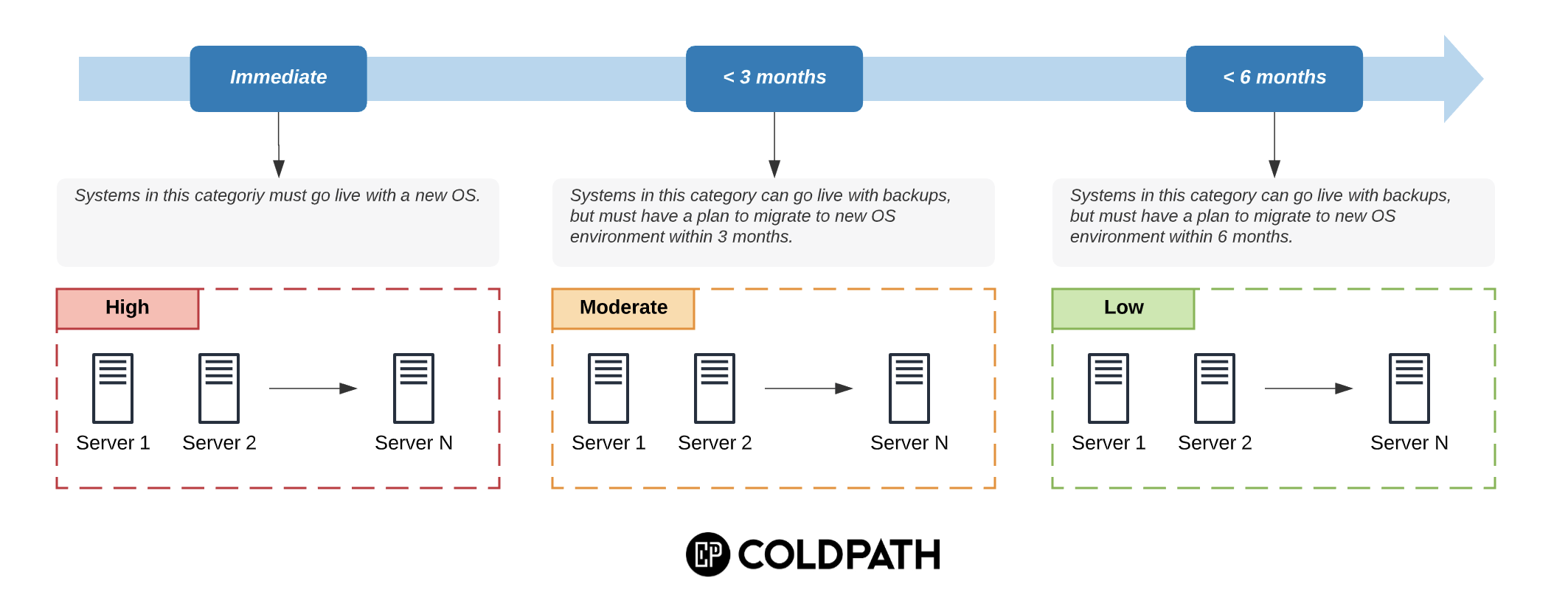
If you are an agency building websites for your customers, and managing those sites on a Virtual Private Server (VPS), this post is for you.
While working on a recent forensics case, we encountered one of the most egregious mistakes we see with organizations managing multiple websites on one server.
All websites were owned by the default web server user and group.
[Read more…] about Secure a VPS to Manage multiple Websites – Part I (Isolate Users and PHP)